Everything on a running system – the operating system, running programs, files, everything – exists within system memory during runtime. The only stuff that’s truly running on a system is what’s stored in system memory, making the hard drive totally irrelevant unless we’re interested in historical data as evidence. A live acquisition and the right tools therefore provide an exact reconstruction of the target machine as it was when the capture was made, and this makes Volatility such a powerful tool for digital forensics.
Network Activity
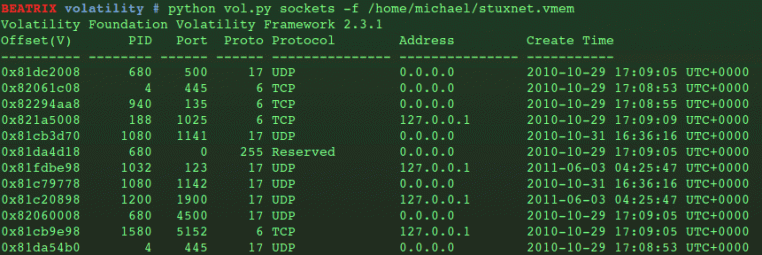
All the basic features we’d expect are there. We can get a list of ports/sockets that were open when the memory dump was acquired, using the ‘
sockets‘ option.
Notice the offsets and process IDs in the first two columns of the output. They tell us roughly where we can find the processes that were using the ports, although I’m guessing there’s an easier way of doing that.
Then we have ‘
connections‘ and ‘
connscan‘, depending on the operating system in question. These reveal the TCP connections that were discovered, the remote and local addresses, and the PID. There wasn’t any information given in the particular memory dump I was looking at, which makes sense if the STUXNET capture was from an offline machine.